Setup
I started on the CompTIA trifecta in mid 2022, got the A+ (220-1101 & 220-1102) in February 2023, Net+ (N10-008) in Sept 2023, and Sec+ (SY0-701) in April, 2024. I used a mixture of study resources for the exams, but relied heavily on Professor Messer’s great practice exams, YouTube lessons, study sessions, and Discord channel.
This is a review of the Net+ exam material, with a focus on the CompTIA objectives that are most applicable to actual helpdesk tickets (IMO). I’ll rate each topic on a rigorously subjective scale of 1 - 5 stars (⭐’s).
Exam Overview
CompTIA N10-008 Exam Objectives
PERCENTAGE OF EXAMINATION
1.0 Networking Fundamentals 24%
2.0 Network Implementations 19%
3.0 Network Operations 16%
4.0 Network Security 19%
5.0 Network Troubleshooting 22%
1.0 Networking Fundamentals
Objective 1 Overall Score: ⭐⭐⭐
3/5. OSI model, network types, provider link types, and protocols are super valuable material. Cables and Connectors material in 1.3, and IP addressing in 1.4 are both valuable, but dive deeper than I usually need to know for tickets. 1.7 and 1.8 had a lot of buzzword material, stuff that is worth recognizing, but I can’t use it to solve a problem.
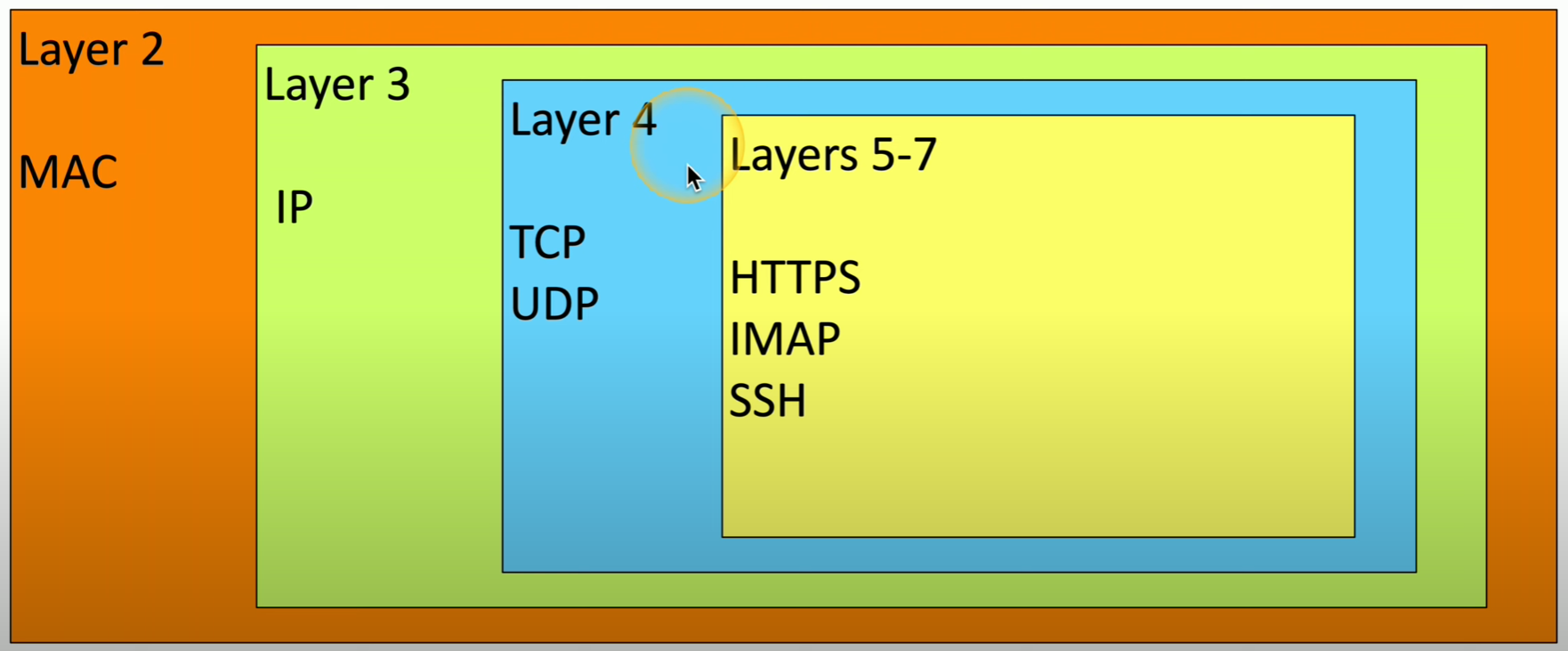
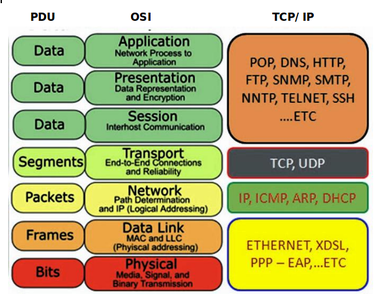
OSI model
⭐⭐⭐⭐⭐
Net+ starts off strong with some of the most helpful, relevant material for troubleshooting out of all three trifecta exams. The OSI (Open System Interconnection) model presents an organized, systematic process for working through networking issues. Which is a great alternative to haphazardly turning stuff on and off again with your fingers crossed 🤞.
Obligatory Mnemonic: All People Seem To Need Data Processing
- Layer 7 - Application
- My understanding of layers 5 through 7 is still a little hazy, compared to 1 through 4. At first, I thought the Application layer was about the GUI an end user interacts with
- But (since this is a networking model), layer 7 is more about the API; the point where the network connects to an app to move data in and out
- This data gets moved by a variety of familiar protocols: HTTP, FTP, DNS, POP3…
- Layer 6 - Presentation
- Character encoding and application encryption?
- Layers 5 through 7 also often get grouped together, and there aren’t necessarily definitive boundaries between them
- Layer 5 - Session
- Starts/stops/restarts communication between devices using control protocols and tunneling protocols
- Layer 4 - Transport
- AKA the “Post Office" layer
- Ports and protocols
- TCP or UDP headers are added to or removed from the data. Data + a TCP or UDP header = a Segment
- Layer 3 - Network
- Aka “Routing layer"
- IP addresses. Add an IP header to a Segment, and you get a Packet
- Layer 2 - Data Link
- MAC addresses, switches, APs, and Frames
- A Frame consists of a Packet, plus a Frame header with the source and destination MAC addresses, and a Frame footer, with FCS (Frame Check Sequence) code to verify integrity of the data
- Layer 1 - Physical
- Ethernet cables, fiber cables, coax cables, connectors, punch-downs, NICs, drops
- All the data in the payload is broken down into bits
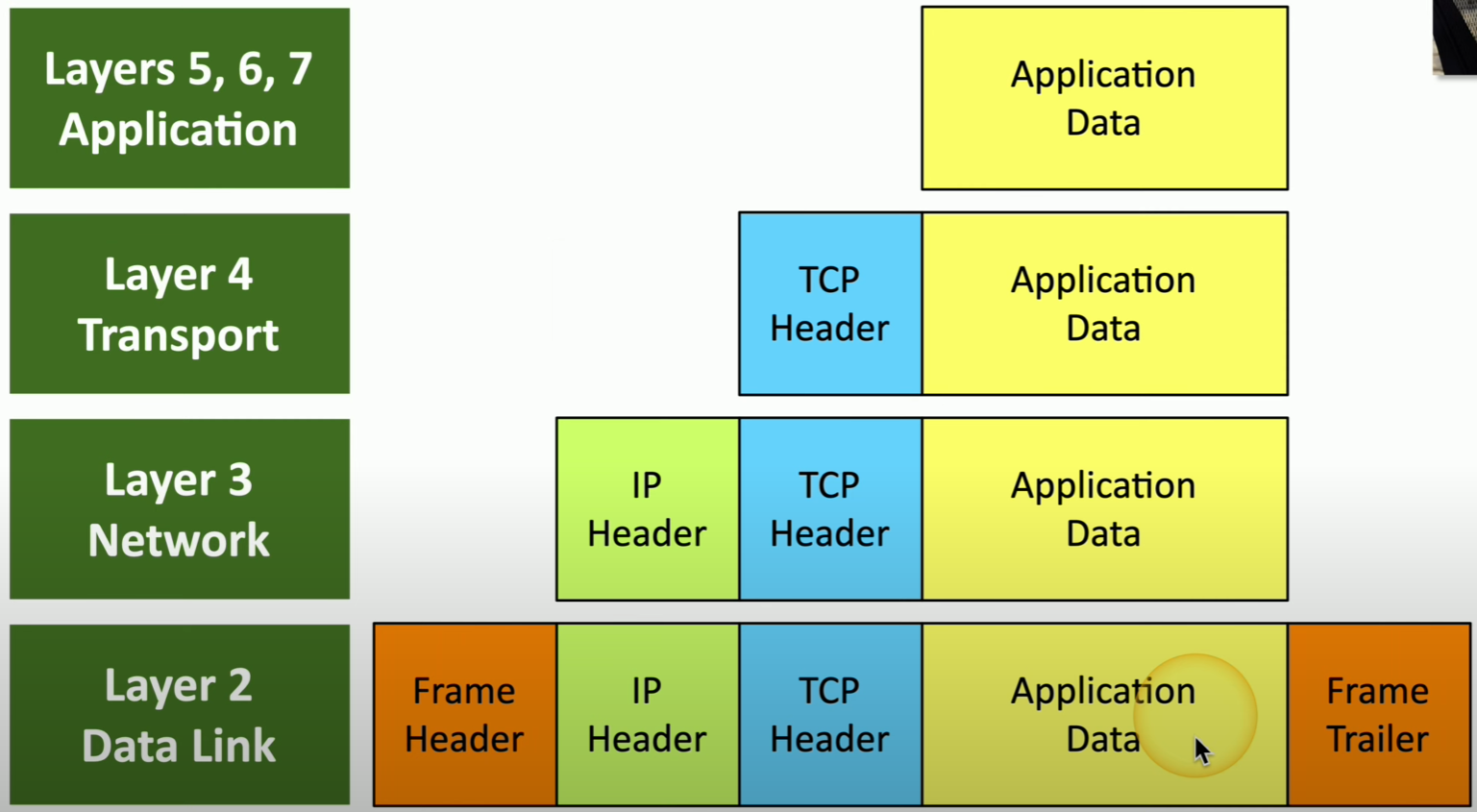
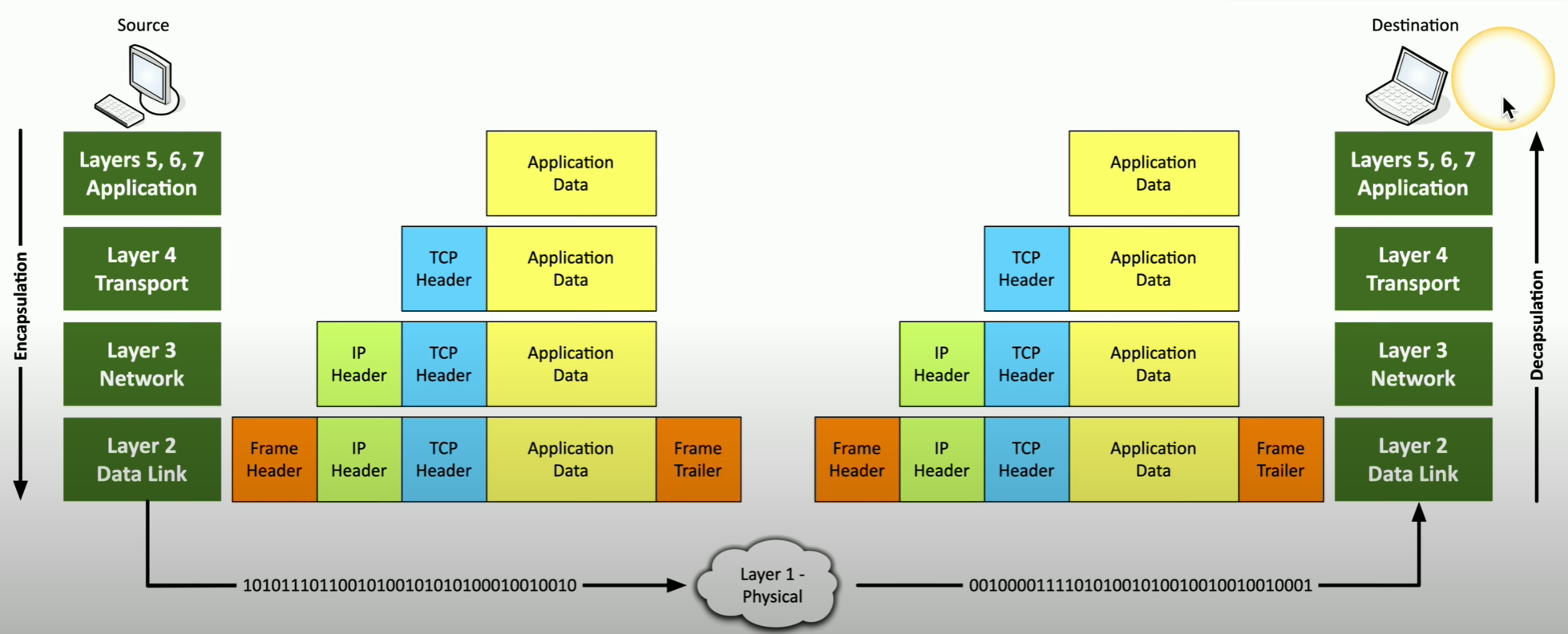
Encapsulation and Decapsulation
As data (the Payload) travels up or down the layers of the OSI model, headers are added and taken away to facilitate where it should go. The different types of units are called PDU’s (Protocol Data Units).
TCP Flags & the 3-Way Handshake
⭐⭐⭐⭐
I’ll give this topic 4/5 stars because it is valuable information, even if I only work on the occasional networking ticket that touches on it. Mostly, I see these flags if I open up Wireshark, or if I see a tcp SYN checking failed log message in the Traffic Monitor of a WatchGuard firewall.
TCP flags - bits that live in the TCP header. They are on or off, and control the data flow
Basic flags for the 3-Way Handshake:
- SYN - Synchronization of sequence numbers from client to server. Initiate the 3-way handshake
- SYN-ACK - Acknowledge the request, and synchronizes sequence numbers back from server to client
- ACK - Acknowledge that packet was successfully received, establishing the connection, and ending the 3-way handshake
Some of the other possible flags:
- PSH - Push data without buffering
- RST - Reset the connection
- FIN - Last packet from the sender. Used to close the client/server connection
Mesh networks, PAN, SAN, vSwitches, Metro-optical…(?)
⭐⭐
In contrast to Net+ objective 1.1, 1.2 serves as an example of the type of objective that felt like a confusing mess of material jammed into too little space.
In reality, the purpose of this entry level exam is just to test if a technician is familiar enough with a broad range of acronyms to guestimate their way through 90 minutes of multiple choice questions. But as I worked through the trifecta, I couldn’t help but feel irritated at the lack of depth on some topics, and the apparent randomness in the way they are organized, at times.
Demarcation Point - Where the WAN connects to the LAN. A common example is the ONT (Optical Network Terminal) that mark the boundary between where the ISPs fiber-optic cable - and their responsibility - ends, and the consumer’s firewall/router take over.
The SOHO environments I work with use a fiber, copper (DSL or cable), or occasionally satellite connections.
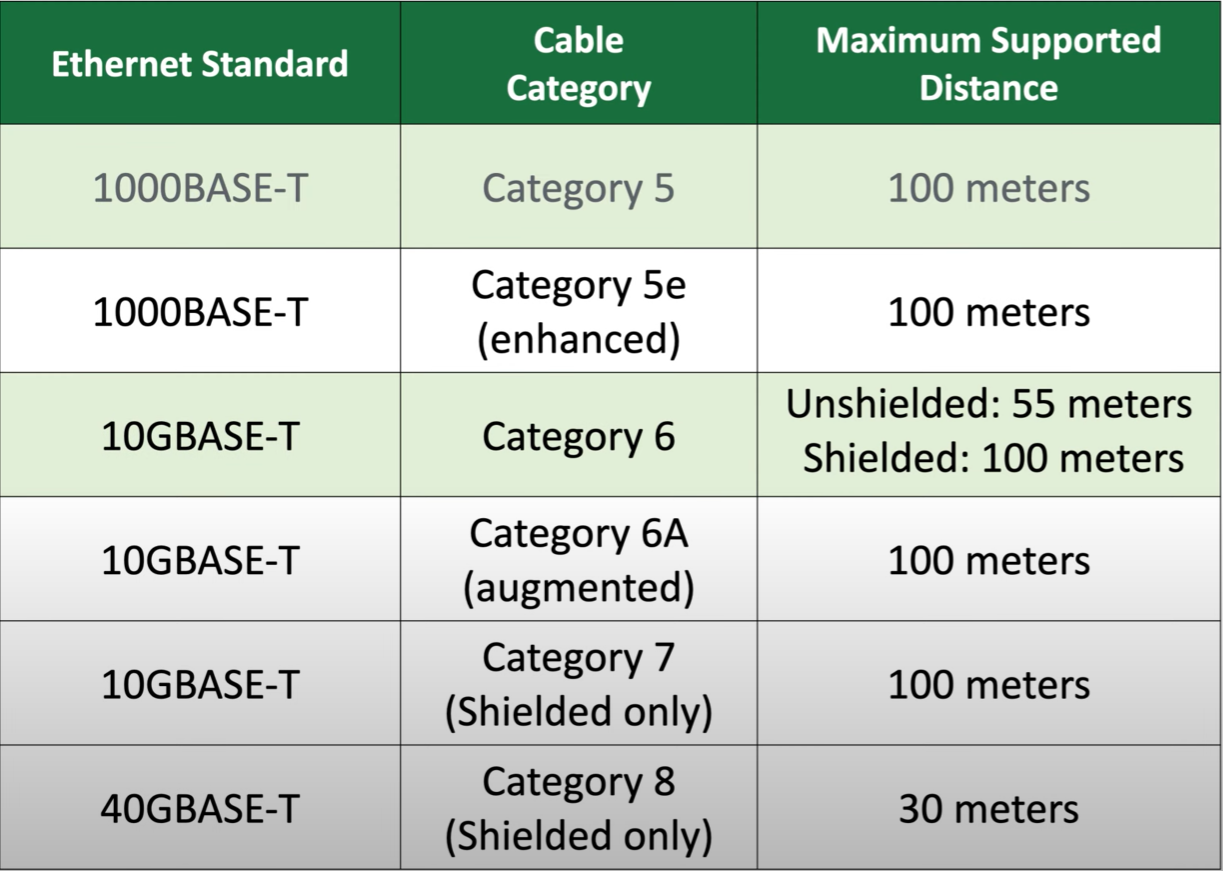
Cable and connector types in objective 1.3 are useful, though I’d rely on that knowledge a lot more if I was working in the field, instead of at the desk.
IP Addresses
⭐⭐⭐⭐⭐
The Net+ required me to calculate a lot of network addresses and convert a lot of slash notation to subnet masks. In reality, I use a subnet calculator and go about my day. But I definitely can’t fault the test for emphasizing it. The material is necessary and useful.
Terminology highlights from this section:
Loopback address - Usually use 127.0.0.1, but the range goes through 127.255.255.254. Send a ping test to your own device to test if the NIC is working, or set it on a domain controller as the primary DNS address provider
Reserved addresses - Class E addresses, 240.0.0.1 through 254.255.255.254. These are set aside for testing. So if you were thinking about reserving one for a shared printer, don’t do it.
APIPA - Automatic Private IP Addressing. 169.254.0.1 - 169.254.255.254. Vital to keep an eye out for 169 IP addresses. Network adaptors get assigned one of these if DHCP isn’t available. E.G. the network drop the janitor plugged the CEO’s Canon into isn’t actually connected to a working switch.
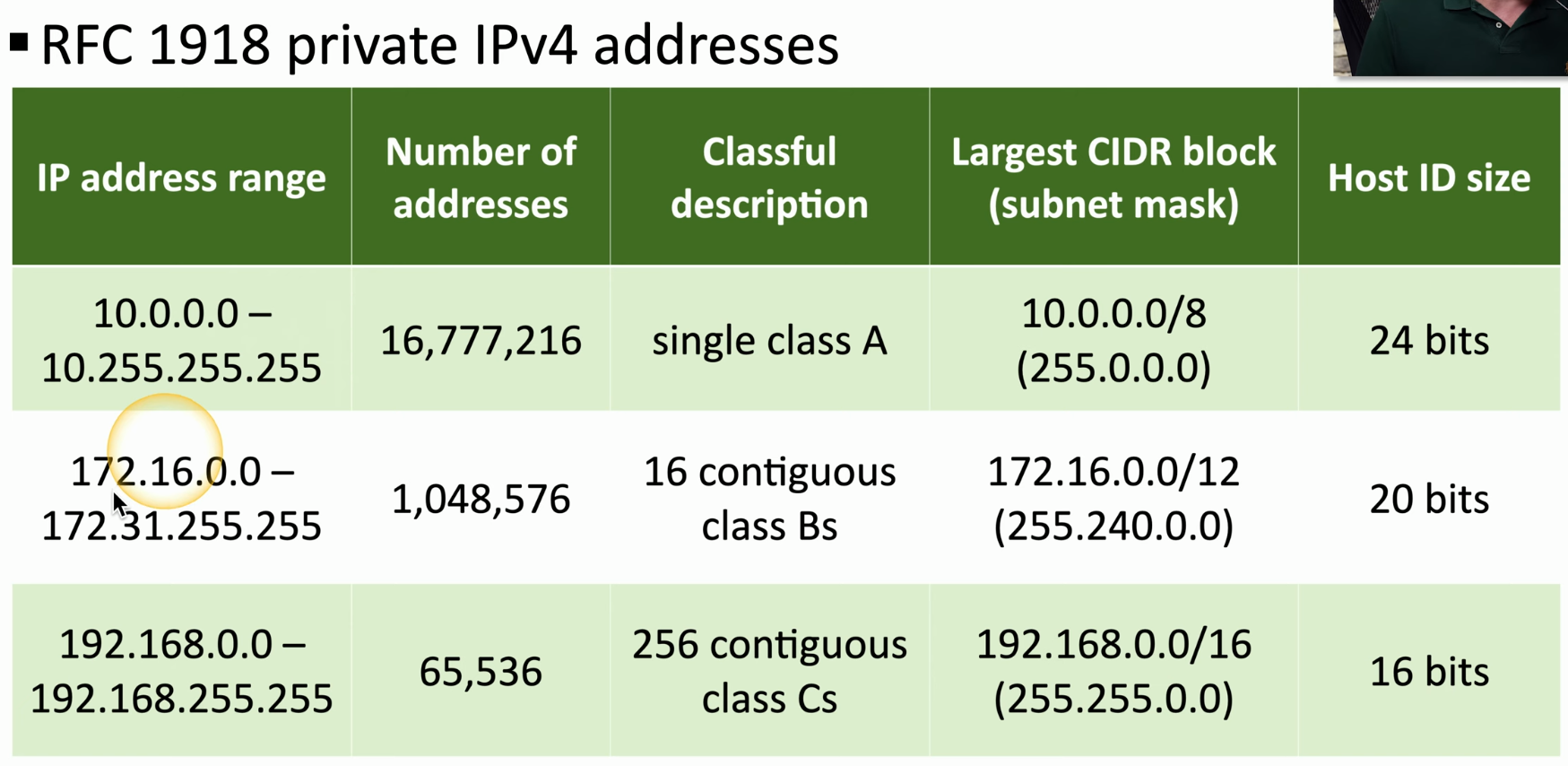
NAT - Network Address Translation. IPv4 only supports 4.29 billion addresses, and humanity already has 20 billion devices online. So all the LAN devices, which “sit behind NAT” or are “NAT-ed”, get an IP in the private range
PAT - Port Address Translation. NAT’s little brother. E.G. To load up Facebook, you make a request from your phone, and their server responds to the public IP address assigned by Comcast to your home router. Your router figures out both how to send the website to your phone, not your roommate’s IoT smart-toaster, with NAT. And it sends the response to port 443, so you can view the web page, with PAT.
Bonus: The world is slowly transitioning from IPv4 to IPv6. But why did we skip IPv5? It was developed, had a bunch of limitations, and got skipped over entirely.
Subnetting
Using 192.168.0.1/24 as an example:
- Network Address
- 192.168.0.0
- First IP address in a subnet
- Won’t get assigned to a device with DHCP. Used to identify the subnet, and for routing
- First Usable Host address
- 192.168.0.1
- Usually the router, but that is just convention
- Last Usable Host Address
- 192.168.0.254
- Last address a device on the subnet can lease out
- Network Broadcast Address
- 192.168.0.255
- Used to send packets to every device on the subnet, like ARP requests
Ports and Protocols
⭐⭐⭐⭐
Valuable material. Only gets 4/5 stars because the first half of the A+ already covered most of it.
DNS - Domain Name System. “It’s always DNS.” Someone’s gotta translate all the IP addresses to domain names.
Would be nice if the Net+ actually dug more into troubleshooting DNS. Pinging by IP vs hostname vs FQDN, checking A records for endpoints in an on-premises domain, figuring out if the firewall decided to start blocking traffic to Cloudflare for some esoteric reason.
If a client workstation sends a DNS request to its DC, and the DC proxies that request out to a name server, that is a typical recursive request. If the workstation asks the name server itself, that is an iterative request. If you run an nslookup for a domain and get an authoritative answer, you’re getting a response directly from the name server. If you get a non-authoritative answer, you’re seeing the cached response your DNS provider remembers from the last time someone asked. A forward lookup uses the FQDN to ask for an IP. A reverse lookup uses the IP to ask for a FQDN.
When DNS is broke, 99% of the time a tech should…
- NOT edit the hosts file, the DNS equivalent of duct taping a garbage bag over a busted car window
- NOT set the workstation NIC to use some specific DNS servers to workaround what should already be working on the default gateway
- NOT map the printer by TCP/IP and hope it never gets unplugged for 5 minutes and loses its preferred IP address
- Probably check the domain controller, see if it fell off the domain and is on a private network, and restart NLA
- Definitely ping everything from everywhere else until something that should respond doesn’t
Objectives 1.7 - 1.8 - SDN, SAN (again)
⭐⭐
Back down to 2/5 stars, IMO. Maybe SDN (Software Defined Networking) would mean more to me in another job or the right context. But EVERY CompTIA exam in the trifecta has covered this topic, and I’ve yet to really grasp why the distinction between “Application layer” and “Data plane” is useful.
Also not sure why we are doubling back on SAN material, instead of combining it all in 1.1 or 1.8 ☹️
2.0 - Network Implementations
Objective 2 Overall Score: ⭐⭐⭐⭐
4/5. Great objective. Lots of repeat material from the A+, and some general terminology about specialized subjects that aren’t for general use. Some of the material in Objective 2 falls into the category of general jargon and shallow overviews of specialized topics (SCADA, dynamic routing protocols, etc.). But Professor Messer and Mike Meyers go into sufficient detail on the most important topics to make this part of the exam really meaningful for helpdesk work. 5/5 stars.
Networking Devices
⭐⭐⭐⭐⭐
Hub
Hubs are antiquated technology, so at first glance I thought it was a waste of time to cover them on the Net+. In retrospect, learning about hubs provides helpful context for WHY we use switches and routers.
Hubs only work at layer 1 of the OSI model, and aren’t even aware of MAC addresses. They broadcast out the same traffic to everyone hooked into them, and it is up to the endpoints to read the MAC address on the frame and determine if it should load up a webpage. But if it was still 1995, at least the hub could facilitate a primitive network.
Hubs always operate at half-duplex (data is either coming or going, not both at once)
Bridge
Example: An AP, which “bridges” a wired Ethernet connection to a wireless radio transmitter. Overall, more like a concept than a specific type of device.
Switch
Switches are rough on the helpdesk. They operate at layer 2 of the OSI model, and are next to invisible from the POV of remote troubleshooting. Better hope they are documented. A field tech, on the other hand, runs into them constantly.
Still, switches are a satisfying topic in their intuitive, functional purpose. At the end of the day, they are just a bunch of ports to plug stuff into. They solve the very physical problem of dragging miles of cables around everywhere.
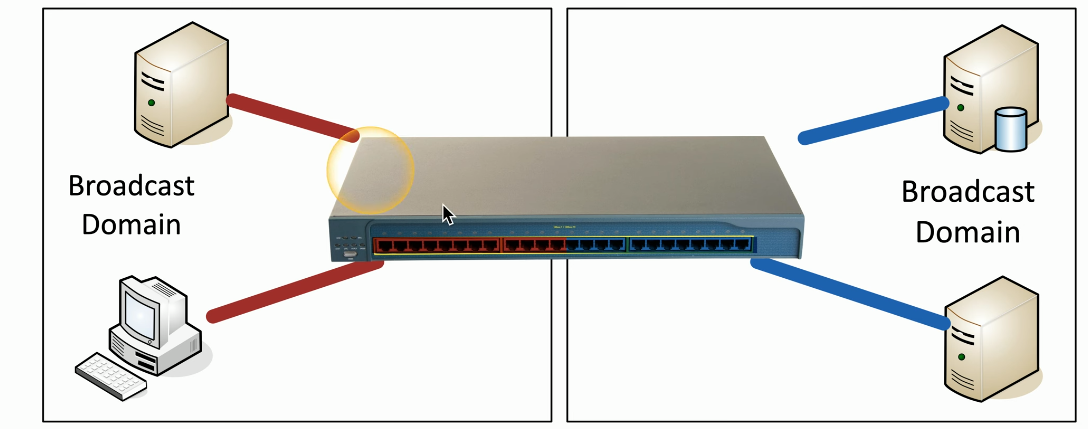
Each interface on a switch is its own collision domain, like a hub. By default, all interfaces on a single switch belong to a single broadcast domain.
Switches build their tables associating IP addresses with MAC addresses using ARP (Address Resolution Protocol).
If all the link lights are flashing in unison, you’ve got a broadcast storm. Configure STP (Spanning Tree Protocol) just in case you accidentally connect two switches and make a loop. Secure switch interfaces with NAC (Network Access Control).
Modem / Router / Firewall / APs
I’m clumping these together, because as recently as a couple of years ago, they were interchangeable in my mind. Which is perfectly understandable; from a layman’s perspective, you usually get a gateway device from your ISP, and it does all four jobs.
Modem converts signal from ISP, and often serves as the demarcation point. Router directs traffic through the LAN, as well as out to the LAN, runs NAT, often serves DHCP. Firewall watches the traffic and applies security rules. APs produce a WiFi signal.
The distinctions between those four types of devices are, of course, imperative when working helpdesk tickets. If the problem is the modem, reboot it, and if it still doesn’t work, thank god, it is the ISP’s fault.
I work primarily with WatchGuard firewalls, which are stateful (i.e., smart, aware of traffic streams and previous packet activity) and qualify as NGFWs (Next Generation Firewall; can block by layer 7 application data, rather than just port number)
Proxies
⭐⭐⭐⭐
Important to understand as a concept (rather than a specific device, doing a single job).
A proxy is basically a MiTM / on-path attack, even when it is being used legitimately. It intercepts traffic. Often a device, like a proxy server, but could also be a policy, or other type of system.
A Forward Proxy sits between a user and the internet. Might be an internal proxy, like at school to block streaming services.
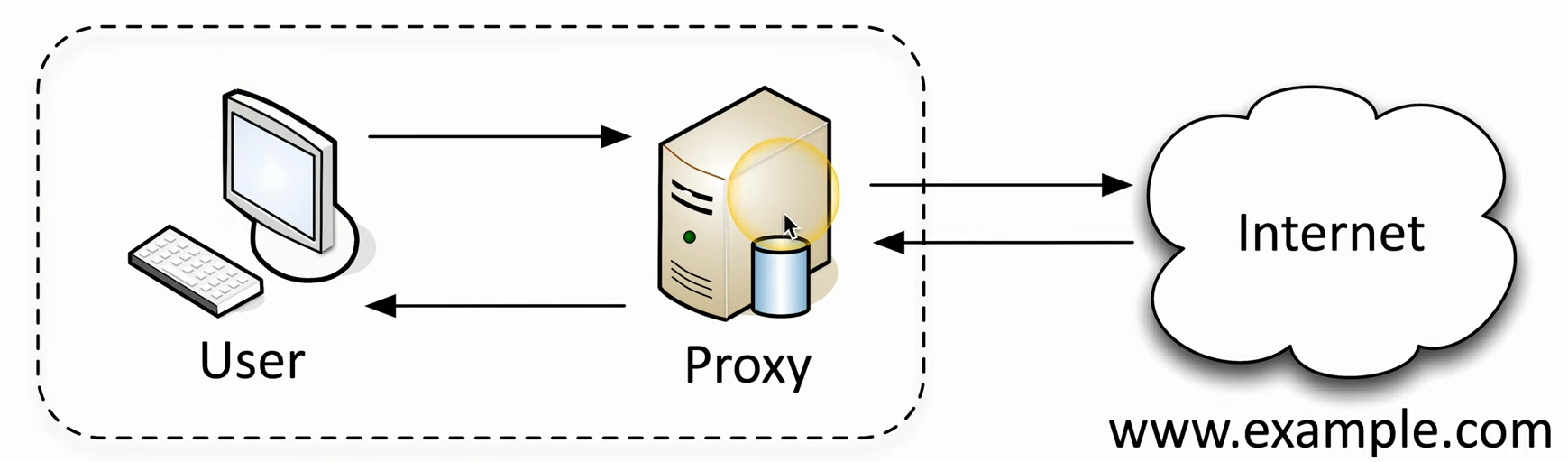
A Reverse Proxy sits between a web server and the internet. It is a taste tester, or guard. It intercepts traffic, passes it along after checking it. It can respond with cached results back to requests from the internet to save resources.
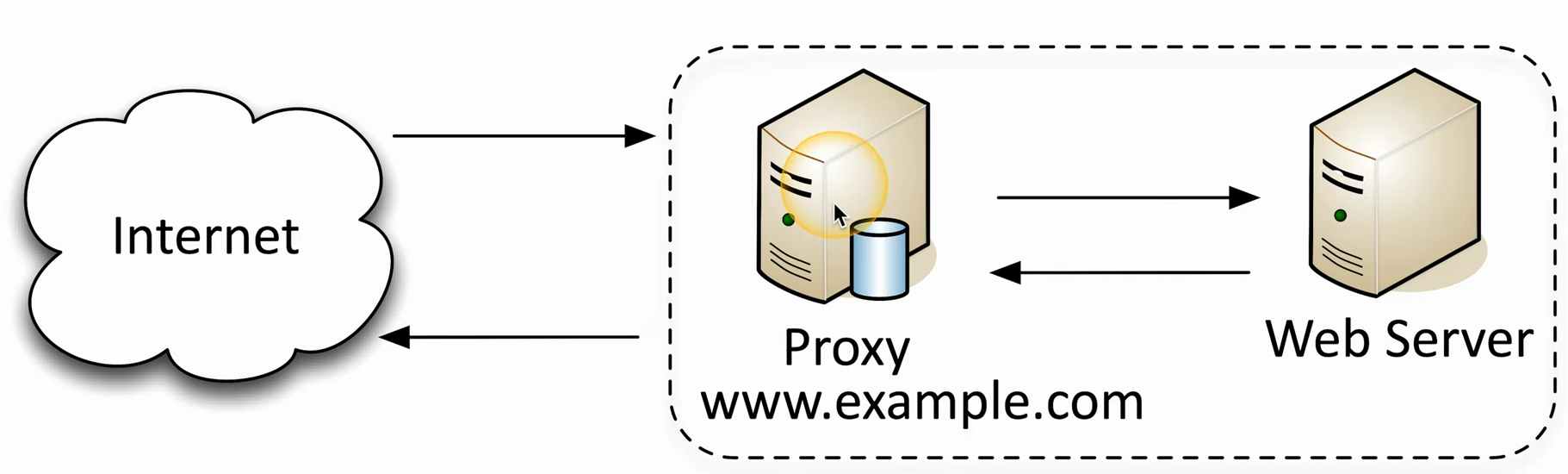
Routing Concepts
⭐⭐⭐
3/5, useful for general knowledge, not something I put into practice often. Seems more like an introduction to material an experience network engineer would use in an enterprise-level environment.
A hop is a packet passing a router. Any single router only needs to be aware of the next hop. Routes are recorded in Routing Tables, and SOHO environments only usually need a few entries for directing traffic from VLANs. Convergence happens when all the routers on a network have exchanged routing tables and agree on what the network topology looks like.
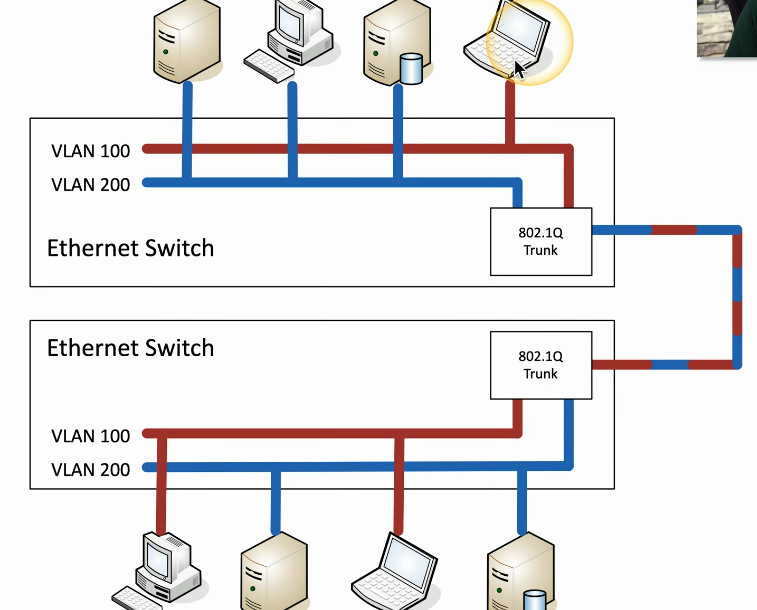
VLANs / Trunking / LAG / Mirroring
⭐⭐⭐⭐
Instead of using two switches to create entirely different physical LANs, use logical VLANs to separate them out

The switch inserts another header into an Ethernet frame to identify which VLAN it is on

Can also use trunking to connect two switches and organize various devices plugged into each of them. Might do this to separate out VoIP devices, IoT devices, workstations, and servers
LAG (Link Aggregation) / Port Bonding - Connect two switches together with several cables to increase throughput
Port Mirroring - Copy all the traffic going through an interface for packet captures or intrusion detection. Might collect that data with a SPAN (Switch Port Analyzer Connection) or a physical network tap
Wireless
⭐⭐⭐⭐⭐
SSID and BSSID and ESSID and IBSS
The Service Set Identifier is the name of the wireless network. An end user sees one, homogeneous SSID, when in reality their phone might connect to different APs depending on where they stand. BSSID (Basic SSID) is the term for a network from a single AP. ESSID (Extended) is the term for a network from multiple APs. IBSS (Independent Basic Service Set) is when two devices talk directly by 802.11 without an AP facilitating the connection.
IEEE 802 standards
⭐⭐
2/5 stars because these Eye-Triple-Eee standards are tremendously convenient for test-writers, but not commonly used in real life, apart from the occasional section heading in a switch GUI.
The only real-life use case for an actual technician to say “We need to fix 802.1d” instead of “We need to fix STP” is to exhibit to everyone in hearing range that they know what “802.1d” means.
- 802.1d = STP
- 802.1q = VLANs and trunking
- 802.1x = NAC / Port security
- 802.11a - 802.11ax = Wireless standards
- 802.11w = Encrypting management frames (used with WiFi to find APs, etc.)
- 802.3ad = port bonding/link aggregation
- 802.3af = PoE
- 802.3at = PoE+
Crossover Cables
⭐
Again, if I was a field tech, I might care more about this topic. But the amount of time spent expounding on why everyone is wrong about crossover cables having 568A on one end and 568B on the other seems unnecessary.
3.0 - Network Operations
Objective 3 Overall Score: ⭐⭐
2/5. Plenty of jargon and acronyms that are worth memorizing for a test so, hopefully, 6 months later you still retain a general gist of what they are used for. Not a fan of the cursory overview of “Plans and procedures” or “Availability Concepts”.
SNMP
⭐⭐⭐⭐
4/5. Most informative section in Objective 3. Good information about interface errors:
- Runts
- Frames that are less than 64 bytes
- Might be caused by a collision
- Giants
- Frames more than 1518 bytes
- Unless you are using jumbo frames
- CRC error - Cyclic Redundancy
- Failed the Frame Check Sequence
- Checks if raw data was accidentally changed in transport
- Might be a bad cable or bad interface on a switch
Plans and Procedures, Common Agreements
⭐
1/5. If you are in a role that requires making these plans, you’ll need a much deeper knowledge about them. If you aren’t, the names of each type of plan are descriptive enough on their own.
Availability Concepts
⭐
1/5. Memorizing the arbitrary distinctions between RTO and RPO isn’t going to be worth anyone’s time.
4.0 - Network Security
Objective 4 Overall Score: ⭐⭐⭐⭐
4/5. Good material, interesting stuff, gets covered in more detail in Sec+.
Vulnerabilities
⭐⭐⭐
3/5. Not really something I have to spend much time on, but good to know about. Sec+ goes into a lot more depth.
NVD (National Vulnerability Database) run by NIST (National Institute of Standards and Technology). Website: nvd.nist.gov
Attacks
⭐⭐⭐⭐⭐
5/5, interesting and useful. Several of the attack types can just happen accidentally due to an in advertent networking issue.
MITM - Man-in-the-Middle - AKA an On-Path attack. Think “proxy”. Someone is capturing traffic before it can get to the intended destination. This is a general term for a variety of attacks in different contexts. ARP Poisoning captures traffic by spoofing the IP:MAC address relationship. DNS Poisoning modifies DNS records, or a workstation’s host file.
VLAN Hopping. Send a packet with two VLAN tags, after the first switch processes and removes the first VLAN tag, which reveals the second tag, and tells the switch to forward the packet to another switch, and into a secure VLAN.
DoS - Denial of Service. Also a general term for a lot of subcategories. For example, Wireless De-authentication, where the attacker uses management frames to kick a device off the WiFi over and over.
4.4 - VPNs and remote access
⭐⭐⭐⭐⭐
5/5. Work with VPNs, SSH, and out-of-band management systems all the time. Would have liked to go into greater detail on this material, and skip some of the physical security material.
A Client-to-Site VPN facilitates a remote worker accessing a 1.6 GB Excel spreadsheet from a company shared drive while they vacation in Bora Bora. It is either broken because they need to change their password, or because they forgot to sign into the VPN client application.
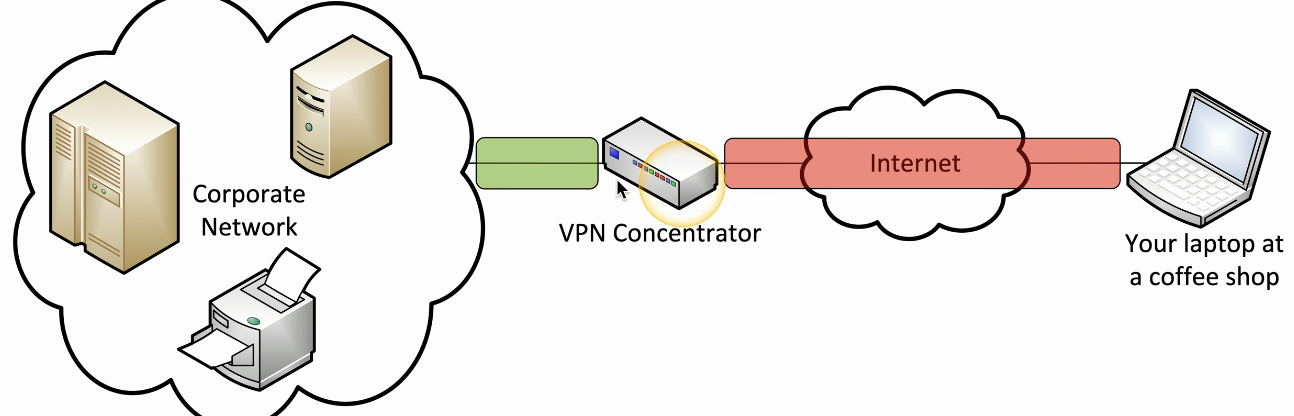
A Site-to-Site VPN connects branch offices to the same central File Server. It is broken because the power at the Bora Bora office has been out for 3 days, or because the central Dallas office forgot to pay the ISP bill.
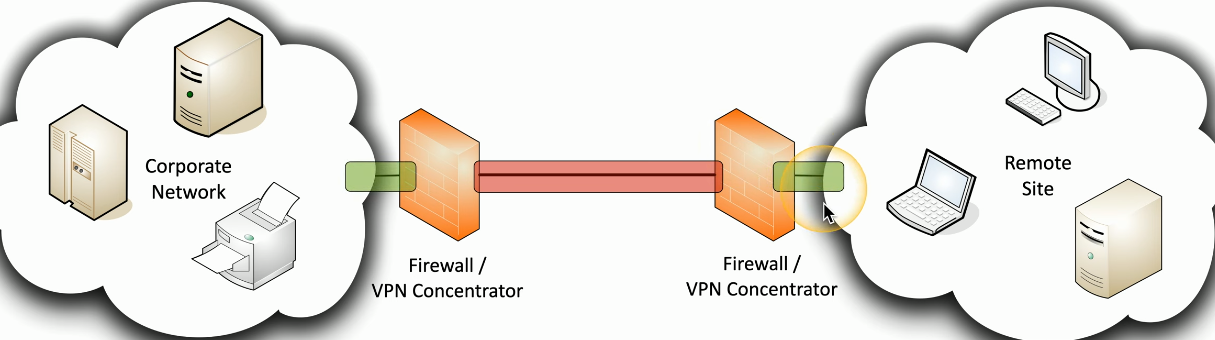
The concept of a VPN Concentrator threw me off for a while. In smaller businesses, a firewall that also has VPN features is the concentrator. At enterprise scale, it might be a separate network devices that specializes in large numbers of connections, and scales up easily.
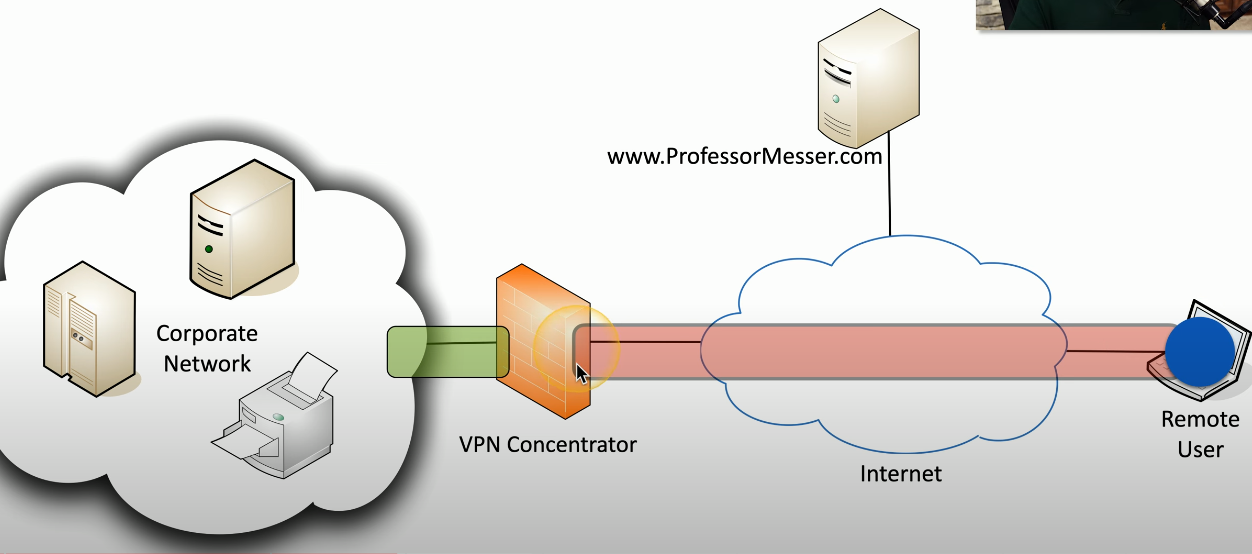
Full Tunnel - When the VPN client is turned on, all traffic to other web servers also goes to the concentrator, through the corporate network, out to the third-party target
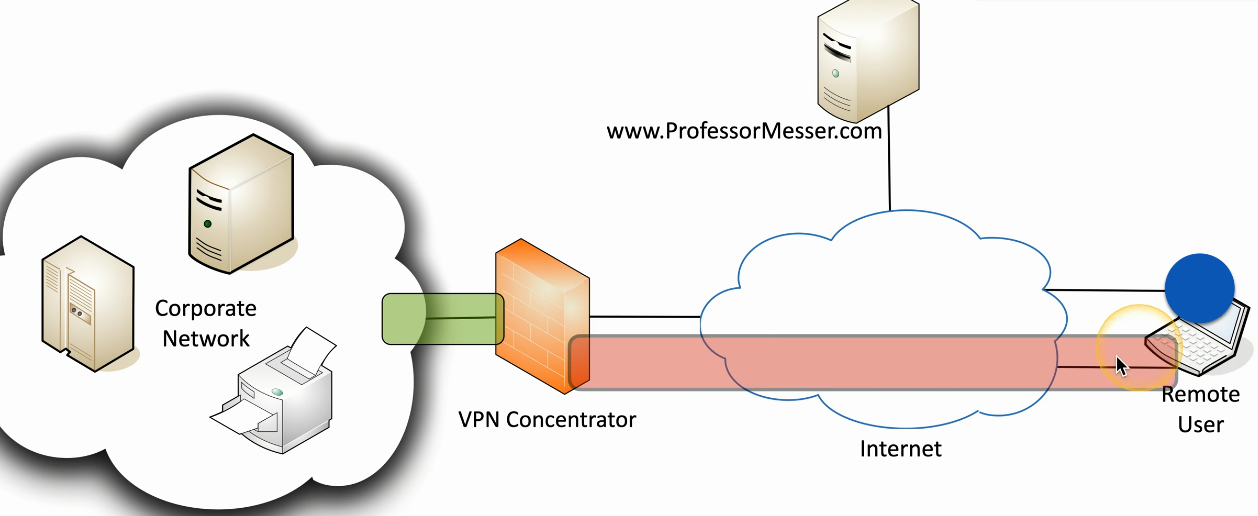
Split Tunnel - Traffic to the corporate network goes through VPN, but other normal web traffic gets routed directly as it normally would if the VPN client was off. Might be handy to conserve limited corporate resources.
Physical Security
⭐⭐
2/5 might not be fair, but, again, while it doesn’t hurt to give an overview of how cameras and locks and asset disposal fit into overall security posture, most of the material feels obvious, and too generic to apply to a ticket.
5.0 - Network Troubleshooting
⭐⭐⭐⭐⭐
Easy 5/5. Outlines effective methods for fixing problems. This is the material I look for when I choose a certification, as well as the material that hiring managers should value when they consider a candidate for a position.
Troubleshooting Methodology
⭐⭐⭐⭐
Solid 4/5. This is, indeed, an accurate description of the process when working a helpdesk ticket. One star withheld because the exam questions tend to test for your ability to memorize the order of the steps, not your ability to apply them in a useful way.
Command Line Tools
⭐⭐⭐⭐⭐
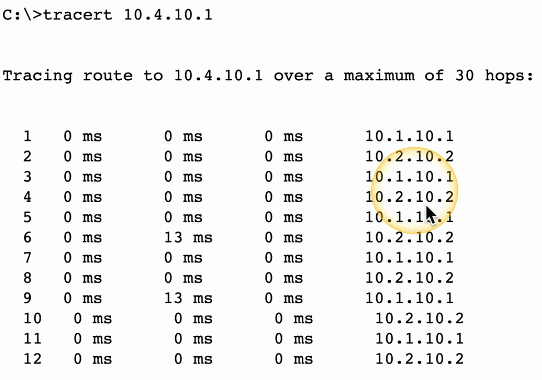
5/5. Ping, ipconfig, tracert, arp, route print, nslookup
Diagnose a routing loop with traceroute:
WiFi performance
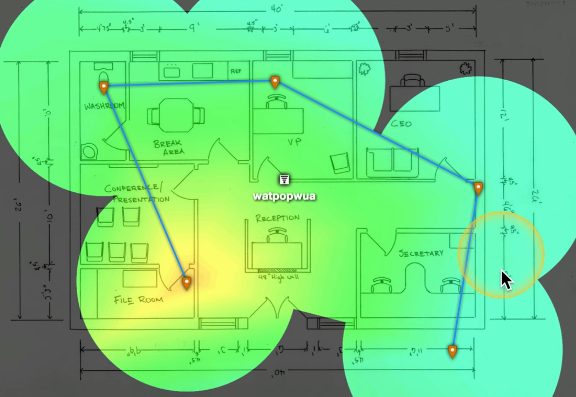
⭐⭐⭐⭐
RSSI is Received Signal Strength Indication, the strength of received signal measured in dBm (decibel milliwatts). The result will be a negative number on a logarithmic scale, closer to 0 is better.
- -50 dBm is excellent
- -70 dBm is good
- -80 dBm and less is low
Noise Floor is unwanted signal from other devices, microwaves, buzz of activity in frequency range. Check Channel Utilization to see if they are overlapping. Perform a Site Survey to get details about reception. If an older device won’t connect to a new AP, check for security / encryption mismatch (an ancient printer might only be able to use WEP).
Common Issues (and random Obj. 5 Vocabulary)
Bandwidth vs Throughput
Bandwidth is the theoretical max speed of data that should be able to fit through a connection. Throughput is the actual amount of data in a given timeframe.
Both are usually measured in bits per second (100 Mbps download / upload speed from the plan you purchase from your ISP). But note that file transfers on a computer are usually measured in Bytes, aka MB/s.
Attenuation. Signal degrades over distance (whether with RF, fiber or copper). Attenuation is measured in dB.
EMI is Electromagnetic Interference inside a copper cable. To prevent EMI, don’t staple, twist, or stretch cable. EMI can also be caused by power cords or fluorescent lights.
Duplicate MAC addresses could be a sign of an On-Path attack, or just a honest mistake by a manufacturer. Duplicate IP addresses are a common issue, especially if a printer is configured to use a static IP that wasn’t reserved for it, and isn’t outside DHCP scope.
If devices keep losing their internet connection, especially mobile devices on a busy public WiFi network, check for DHCP scope exhaustion. If all the leases are claimed, you need to increase the size of the pool, or decrease the lease time an IP address isn’t claimed long after a device requires it.
Bonus Material
Study material I compiled that helped me out on the exam.
DVSA - Differentiating Visually Similar Acronyms
- CCMP vs CSMA/CD vs CSMA/CA
- CCMP is a protocol used with WPA2 for encryption
- CSMA/CD is an old system for dealing with collisions on a hub-based half duplex network
- CSMA/CA = Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) is a protocol for carrier transmission in wireless networks. It reduces collisions when two or more stations send their signals over a data link layer
- SSL/TLS vs SSH vs TCP vs TLL …
- SSL/TLS is about authentication/encryption in VPNs
- SSH is terminal access on port 22
- TCP is one of the two primary protocols
- TLL - time to live is a concept that gets applied in a lot of areas, like DNS records and ICMP
- ICS vs IDS vs IPS
- ICS is an Industrial Control System, so not a firewall or security device but the hardware and software running a factory
- ICS probably won’t get many patches, maybe should be completely separate from external or even internal network, doesn’t get updates, etc
- Uses SCADA networks for sensors and control systems over a large geographical area
- IDS/IPS = Firewall stuff
- NIDS just means Network Intrusion Detection System
- ICS is an Industrial Control System, so not a firewall or security device but the hardware and software running a factory
- BCP vs BGP vs BPDU
- BCP - Business Continuity Plan, random corporate jargon
- BGP - Hybrid routing protocol that can work with WAN
- BPDU - Data units used by STP
- LLDP vs L2TP vs LDAP vs LACP
- LLDP is a protocol that lets layer 2 devices advertise and discover each other
- LT2P is a tunneling protocol, like IKEv2 and GRE and openvpn
- LDAP is Active Directory
- LACP is link aggregation, hooking switches up by multiple cables
- PPP vs PPTP
- PPP is point-to-point protocol, which is used with PPTP and L2TP
- PPTP is point to point tunneling protocol, and is obsolete (?)
Duplicated Terminology
- Poisoning
- ARP or DNS poisoning are types of ATTACKS (On-Path)
- Route Poisoning is a useful networking maneuver. You “poison” a route by setting its max allowable hop count to an unusable number, so the route is advertised as unreachable. This prevents a router from sending packets to hops that are unavailable/invalid
- Split Horizon
- DNS - Use different DNS servers for internal/external networks
- Routing - Avoid routing loops by manually shutting off some possible routes (using hop count)
- TTL - Time To Live
- In the context of ICMP and ping tests, TTL is how many hops before quitting
- In the context of IP routing, a decrementing counter to avoid infinite loops
- In the context of a DHCP lease, how long before it is refreshed and updated with new IP addresses
- In the context of DNS records, how long the A or MX should be cached by DNS servers
- PDU
- Protocol Data Unit
- Power Distribution Unit
Colloquialisms and Jargon
- “Ethernet”
- UTP and other copper cable isn’t actually “Ethernet” cable. Ethernet is a protocol, a standard for how to transmit packet of data. It works over fiber-optic, coax, WiFi, microwave, powerlines…
- Subnets
- Subnets are often referred to as “networks” (e.g. configure the VPN to use a different “network” when switching from 10.0.0.0/8 to 192.168.0.0/24). To be more precise, a single network might use different subnets. Thinking about the root words “sub-network” is the most clear option
- VLANs and subnets often get conflated, which is fair, since usually a VLAN is configured to be on a different subnet out of convenience/convention
- “On the wire”
- Or “The wiring”. Shorthand for physical cabling and Layer 2 network equipment
- E.G. “Separate the network into multiple VLANs so broadcast traffic doesn’t go to everyone on the wire.”