PINs and Passkeys
Scenario:
One user logs into their domain-joined, Windows workstation with a 10 character password consisting of numbers, letters, and special characters, based on complexity requirements set by Group Policy, along with history restrictions and expiration dates.
Another user logs into their identical domain-joined Windows workstation with a 4 digit PIN number, with no restrictions configured whatsoever. AND they use the same 4 digit PIN to unlock their corporate Salesforce, Dropbox, and Intuit accounts. And their personal bank account. They never have to change the PIN, because it never expires. And the 4 digits are their birthday.
Q. Which user has a better security posture?

A. Bizarrely enough, it’s the second user with the 4 digit PIN. They’re logging into their PC with Windows Hello, which is (ostensibly) “enhanced security” featuring…
- Phishing resistance
- Brute-force resistance
- Inherent MFA
- No vulnerable credentials being transmitted across the network or stored on a server
…all of which I find to be counterintuitive, when, in practice, typing in a PIN looks exactly like typing in a password. Except, if anything, easier and less secure.
I’ve worked on tickets involving Windows Hello, FIDO2, and passkeys for years, but learning just enough to fix broken stuff often leaves a lot of gaps in understanding, so I did some reading to fill in the blanks:
Why is the PIN actually better than the password?

TLDR; Because of the way it works behind the scenes. Just trust me.
Windows Hello methods (PIN, facial scan, fingerprint, etc.) are all tied to a specific device. If you write your PIN down on a sticky note and slap it on your monitor, a bad actor could use it to sign into that computer, but couldn’t take it and use it anywhere else. Whereas, if your password was on the sticky note, they could use in a variety of ways, from anywhere, from any device.
The PIN is also local. When you use it to sign into your computer (and thus, your domain account with all the printers and server share access that comes with it), the actual authentication is done with a private/public key pair.
But the password (even if it has a few more characters that would potentially make it harder to guess) isn’t local. It is stored on the server, and transmitted across the network during login attempts. Even though the actual password is hidden by a hash, that hash is more vulnerable to offline brute-force attempts.
All that being said, a PIN is still Something You Know. It is basically just a necessary backup option to supplement Something You Are. Thinking about the other Windows Hello methods, and passkeys in general, makes it easier to see why they are improvements:
What exactly is a passkey, and why are we supposed to be using them?

Depends on who you ask.
The FIDO Alliance defines a passkey as an “…authentication credential…that allows a user to sign in to apps and websites with the same process that they use to unlock their device (biometrics, PIN, or pattern).”
Microsoft generally uses the same definition, but in some contexts uses the word “passkey” to specifically mean using a USB drive as a passwordless authentication method.
And, in daily usage, we often think of our mobile phones themselves as the passkey, even if technically speaking the passkey is not the physical object.
In any case, the whole point is to stop accessing anything with a username/password (things you know), and start accessing stuff with things you are or have. That could mean…
- Logging into your computer
- Accessing private domain shares
- Signing into your email
- Or verifying your payment methods on any random, 3rd party app or service
This brings me back around to why Windows Hello is inherently multifactor authentication. Even if typing in a PIN or password look the same, the PIN is actually proving that you have your computer, and know your PIN. If you’re using the recommended primary methods, even better; it proves you are yourself via your face, iris, or fingerprint.
At the same time, using passkeys solves a bunch of other problems. Depend on your circumstances and the platform, passkeys might mean…
- You don’t have to think up a password for a new streaming service, or increase your attack surface by reusing the username and password you’ve used for everything since the late 90’s
- You don’t have to maintain a password manager to store all 1000 randomly generated passwords to all of your streaming services
- You don’t have to get a 2FA code texted or emailed to sign back in to your favorite streaming services after they revoke your session for sharing your username and password with your cousin in Ohio
Is that it?

Basically, yeah. I think about the improvements offered by passkeys in three categories:
- Something you have/are vs. know
- Cryptographic-backend-invisible-software stuff
- Hardware stuff
We already covered #1. Realizing that a PIN is, in a sense, something you have as well as something you know makes intuitive sense. Easy to see why that is an improvement there.
#2 is less obvious, but it is good to know the key exchange going on behind the scenes is fundamentally a more robust system. The particulars of how that key exchange works are beyond the scope of this post, a phrase which here means, “I basically definitely kind of understand it…but not well enough to explain coherently.”
At a high level, the traditional password approach uses a symmetric, shared secret that must match up between the client and server; the asymmetric private/public key pair just exchange a signature that can be definitively validated by the server (same process as SSL/TLS certificates, email encryption, 802.1X, etc.).
#3. Developments in hardware make the whole concept of passkeys possible:
- Mobile phones - Since everyone has a phone on them at all times, it’s a no-brainer to leverage that for signing into Amazon to buy a waffle maker. Before the ubiquity of phones, passkey adoption would have been slower, if it happened at all.
- Trusted Platform Modules - Most new computers are shipped with TPM chips on their motherboards that function as a secure enclave where asymmetric key pairs can be generated and validated inside the device.
- Cameras for face recognition, fingerprint and iris scanners, and specifications for those devices to hold them to an acceptable standard of error.
Am I conflating Windows Hello and FIDO2 passkeys?
Sort of, but they are related. Windows Hello is a system of passkey options within the Microsoft ecosystem, which can then also be extended to authenticate to other web services using FIDO2 (the standard) and WebAuthn (an API for implementing FIDO2).
Microsoft administration generally includes some clunky overlap between methods for authentication, passwordless authentication, and multifactor authentication, as well as methods considered acceptable for SSPR (self-service password reset). Migrating legacy, per-user MFA / SSPR settings to the consolidated Authentication Methods policy simplifies things, to a point.
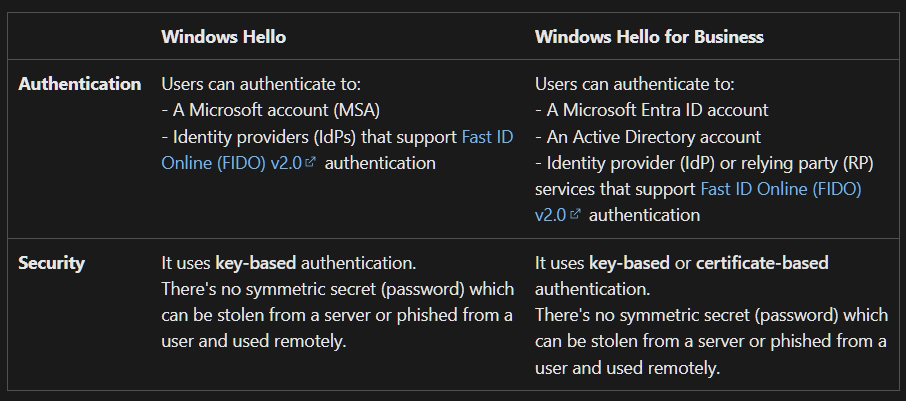
There are also differences in Windows Hello and WHfB:
Honorable mentions and follow-up questions

Q: “Fingerprint scans are one thing, but I’m still not convinced that a PIN is any better than a password.”
A. Fair enough. As you might imagine, I can sympathize with that reaction, since I’m actually the one who posed it.
Q: Since Windows Hello could be used from that specific PC to get to the server and copy confidential files, or leverage other exploits to install malware, isn’t a predictable PIN still a major security risk?
A. Eh. Sort of. I imagine it would be a bigger concern at government agencies or international, enterprise-scale corporations. But this blog focuses on help desk for small to medium-sized businesses. And I can say from experience that I’ve seen dozens of examples of Microsoft accounts compromised by phishing emails that collect login credentials and session cookies, but I could count on one hand the number of times an actual PC was stolen. And never a case where the thief was also able to guess a PIN and use the PC.
Q. Couldn’t the thief just try a bunch of easy PINs to unlock the PC?
A. Doubtful. For one thing, the most basic PINS are never allowed if they have a constant delta pattern. If that’s not enough complexity, you can always set group or Intune policy with most of the same options used for passwords. And, best of all, an attacker can’t run a program to guess infinite combinations due to the anti-hammering in TPM 2.0. If you fail 4 times, you have to reboot. If you keep failing, after every reboot, the device is locked out for 1 minute, 2 minutes, 10 minutes, and so on.
Q. If passkeys in general are so great, why haven’t they adopted by everyone, yet?
Growing pains. The FIDO Alliance provides a lot of the necessary shared rules and standards, but every provider has to decide when to roll it out, when to deal with the inconvenience of helping users set it up, follow the guidelines of their own compliance team, etc.
Q. If all yours passkeys are tied to your device, what happens if you lose it?
A. Good video about that. Basically, you’d just use other, less convenient types of authentication to set the passkey up on a new device. The specifics are going to depend on every platform, and, unfortunately, so far there aren’t reliable norms to provide a uniform experience. Maybe Amazon makes you set up the new passkey with an SMS code (but those are insecure and easy to fake, right?), or maybe Facebook would make you back up the passkey with an old fashioned password (which means it is still stored on the server and also vulnerable to attack, right?). Hopefully you have your passkeys synced to an account and can just restore them by signing into a replacement device.
